Currently Conficker and other malware is taking advantage of the AutoRun functionality as a spreading mechanism. AutoRun is used to start some programs automatically when a CD or another media is inserted into a computer. The main purpose of AutoRun is to provide a software response to hardware actions that a user starts on a computer.
In order to help prevent malware from spreading (such as Conficker) using the AutoRun mechanism, the Windows 7 engineering team made two important changes to the product:
- AutoPlay will no longer support the AutoRun functionality for non-optical removable media. In other words, AutoPlay will still work for CD/DVDs but it will no longer work for USB drives. For example, if an infected USB drive is inserted on a machine then the AutoRun task will not be displayed. This will block the increasing social engineer threat highlighted in the SIR. The dialogs below highlight the difference that users will see after this change. Before the change, the malware is leveraging AutoRun (box in red) to confuse the user. After the change, AutoRun will no longer work, so the AutoPlay options are safe

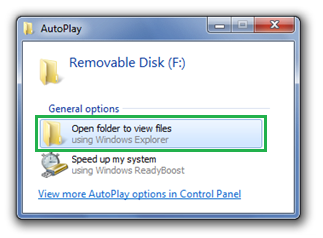
Before the change (left) After the change (right) - A dialog change was done to clarify that the program being executed is running from external media.

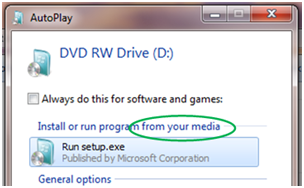
Before the change (left) After the change (right)
For more information please visit the Windows 7 Blog.
source : neowin.net

0 comments:
Post a Comment